
CATEGORIES:
BiologyChemistryConstructionCultureEcologyEconomyElectronicsFinanceGeographyHistoryInformaticsLawMathematicsMechanicsMedicineOtherPedagogyPhilosophyPhysicsPolicyPsychologySociologySportTourism
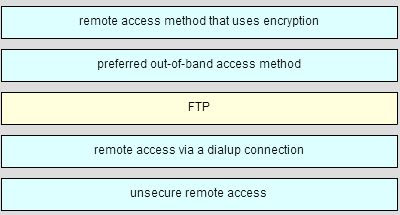
A network administrator requires access to manage routers and switches locally and remotely. Match the description to the access method. (Not all options are used.)
54.

It will give 4 options about ping, the correct one is: The PC2 will be able to ping 192.168.1.1*
55. Which statement best describes the operation of the File Transfer Protocol?
An FTP client uses a source port number of 21 and a randomly generated destination port number during the establishment of control traffic with an FTP Server.
An FTP client uses a source port number of 20 and a randomly generated destination port number during the establishment of data traffic with an FTP Server.
An FTP server uses a source port number of 20 and a randomly generated destination port number during the establishment of control traffic with an FTP client.*
An FTP server uses a source port number of 21 and a randomly generated destination port number during the establishment of control traffic with an FTP client.
56. A client is establishing a TCP session with a server. How is the acknowledgment number in the response segment to the client determined?
The acknowledgment number field is modified by adding 1 to the randomly chosen initial sequence number in response to the client.*
The acknowledgment number is set to 11 to signify an acknowledgment packet and synchronization packet back to the client.
The acknowledgment number field uses a random source port number in response to the client.
The acknowledgment number is set to 1 to signify an acknowledgment packet back to the client.
57. Why does layer 3 device perform the ANDing process on a destination IP and subnet Mask?
to identify host address and destination host;
to identify network address of destination host;*
to identify faulty frames;
to identify broadcast address of destination network;
58. There was also a question about if you activated service password encryption in the past and you prompt “no service password encryption” what password are modified ?
no password at all;*
password of the lines are in clear;
login password;
?
59. What type of communication rule would best describe CSMA/CD?
message encapsulation
flow control
message encoding
access method*
60. What is the primary reason to subnet IPv6 prefixes?
to conserve IPv6 addresses
to avoid wasting IPv6 addresses
to conserve IPv6 prefixes
to create a hierarchical Layer 3 network design*
61. What type of IPv6 address is FE80::1?
multicast
global unicast
link-local*
loopback
62. Which statement describes data throughput?
It is the measure of the bits transferred across the media under perfect conditions.
It is the measure of the bits transferred across the media over a given period of time.*
It indicates the capacity of a particular medium to carry data.
It is the guaranteed data transfer rate offered by an ISP.
63. Fill in the blank. Use a number.
IPv4 multicast addresses are directly mapped to IEEE 802 (Ethernet) MAC addresses using the last ___4___ of the 28 available bits in the IPv4 multicast group address.
64. How could a faulty network device create a source of hazard for a user? (Choose two.)
It could stop functioning.*
It could apply dangerous voltage to other pieces of equipment.
It could explode.*
It could produce an unsafe electromagnetic field.
It could apply dangerous voltage to itself.
65. What are three important considerations when planning the structure of an IP addressing scheme? (Choose three.)
preventing duplication of addresses*
providing and controlling access*
documenting the network
monitoring security and performance
conserving addresses*
implementing new services
66. What is the metric value that is used to reach the 10.1.1.0 network in the following routing table entry?
D 10.1.1.0/24 [90/2170112] via 209.165.200.226, 00:00:05, Serial0/0/0
24
90
05
2170112*
67. Which two services or protocols use the preferred UDP protocol for fast transmission and low overhead? (Choose two)
VoIP*
DNS*
HTTP
FTP
POP3
68. What action does a DHCPv4 client take if it receives more than one DHCPOFFER from multiple DHCP servers?
It sends a DHCPREQUEST that identifies which lease offer the client is accepting.*
It sends a DHCPNAK and begins the DHCP process over again.
It discards both offers and sends a new DHCPDISCOVER.
It accepts both DHCPOFFER messages and sends a DHCPACK.
69. To what legacy address class does the address 10.0.0.0 belong?
Class B
Class D
Class A*
Class C
Class E
70. What type of communication medium is used with a wireless LAN connection?
radio waves
fiber
microwave*
UTP
71. Which method of IPv6 prefix assignment relies on the prefix contained in RA messages?
EUI-64
static
SLAAC*
stateful DHCPv6
72. What is a characteristic of DNS?
DNS servers can cache recent queries to reduce DNS query traffic.*
DNS servers are programmed to drop requests for name translations that are not within their zone.
All DNS servers must maintain mappings for the entire DNS structure.
DNS relies on a hub-and-spoke topology with centralized servers.
73. What is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?
2001:DB8:BC15
2001:DB8:BC15:A
2001:DB8:BC15:A:1
2001:DB8:BC15:A:12
Date: 2015-12-18; view: 4322
| <== previous page | | | next page ==> |
| To prevent faulty network devices from carrying dangerous voltage levels, equipment must be grounded correctly | | | Applications of radiation chemistry |