
CATEGORIES:
BiologyChemistryConstructionCultureEcologyEconomyElectronicsFinanceGeographyHistoryInformaticsLawMathematicsMechanicsMedicineOtherPedagogyPhilosophyPhysicsPolicyPsychologySociologySportTourism
Computer_network
1. A network technician has made a UTP cable that is terminated as T568A on one end and T568B on the opposite end. What type of cable has been constructed?
· Crossover
· Straight-through
· Patch
· Console
· None of the above
2. Which password is automatically encrypted when it is created?
· Console
· Enable
· Vty
· Aux
· Enable secret
3. Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A?
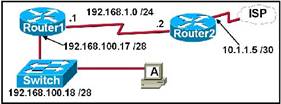
· IP address: 192.168.100.22; Subnet Mask: 255.255.255.240; Default Gateway: 10.1.1.5
· IP address: 192.168.100.30; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.1.1
· IP address: 192.168.100.21; Subnet Mask: 255.255.255.248; Default Gateway: 192.168.100.18
· IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2
· IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.17
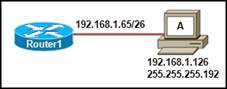
4. A network administrator subnets the network 192.168.1.0/24 into four subnets. Which option correctly addresses Router1 and host A into the second subnet created?
· 
· 
· 
· 
· 
5. Two routers are connected via their serial ports in a lab environment. The routers are configured with valid IP addresses, but they cannot ping each other. The show interface serial0/0 command shows that the serial0/0 interface is up but the line protocol is down. What could be the cause of this problem?
· The interface timers are not cleared.
· The no shutdown command has not been applied to the interfaces.
· The clock rate command has not been entered on the DCE interface.
· The FastEthernet interface is emulating a serial interface by assigning it a timing signal.
· None of the above
6. Which OSI layer does IP rely on to determine whether packets have been lost and to request retransmission?
· Session
· None of the above
· Application
· Presentation
· Transport
7. What is the effect of using the Router# copy running-config startup-config command on a router?
· The contents of NVRAM will change.
· The contents of flash will change.
· The contents of ROM will change.
· The contents of RAM will change.
· None of the above
8. Refer to the exhibit. The router of the company failed and was replaced. After the replacement, hosts C and D in the Education office are able to ping each other, but they are unable to access the hosts in the Accounts office. What is the likely cause of the problem? 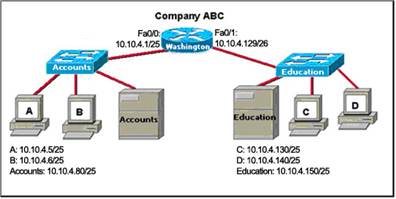
· The IP address at the serial interface of the router is incorrectly configured.
· The hosts in the Accounts office are not on the same subnet as the hosts in the Education office.
· The IP address at the fa0/0 interface of the router is incorrectly configured.
· The subnet mask at the fa0/1 interface of the router is incorrectly entered.
· None of the above.
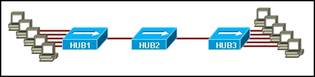
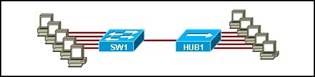
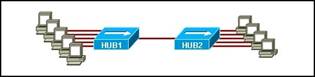
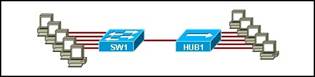
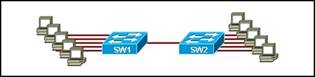
9. Which topology divides the collision domain and provides full media bandwidth to the hosts in the network?
· 
· 
· 
· 
· 
10. Which statement describes the correct use of addresses to deliver an e-mail message from Host B to the e-mail service that is running on Server A?
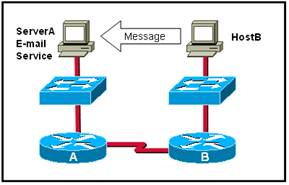
· Router A uses the Layer 4 address to forward the packet to Router B.
· Host B uses the MAC address of Server A as the destination.
· Router B uses a Layer 3 network address to route the packet.
· Via the use of a Layer 3 address, Server A assigns the message to the e-mail service.
· None of the above.
11. Which device should be used for enabling a host to communicate with another host on a different network?
· Hub
· Router
· Host
· Switch
· None of the above
12. Refer to the exhibit. Cable A is plugged into the console port on switch S1. What is required on the PC for a network technician to enter the initial configuration on S1? 
· A web browser
· A telnet client
· A terminal emulation program
· An FTP client
· None of the above
13. A user enters http://www.cisco.com/web1.htm in the address line of a browser. Which statement is true about this transaction?
· The "web1.htm" portion is the specific service name.
· The retrieved web page will be displayed in URL code.
· The "http" portion indicates the protocol that is being used.
· The "www.cisco.com" is the name of the web page file that is called.
· None of the above.
14. Refer to the exhibit. The diagram represents the process of sending e-mail between clients. Which list correctly identifies the component or protocol used at each numbered stage of the diagram?

· 1.MUA 2.MDA 3.MTA 4.SMTP 5.MTA 6.POP 7.MDA 8.MUA
· 1.MUA 2.POP 3.SMTP 4.MDA 5.MTA 6.SMTP 7.POP 8.MUA
· 1.MUA 2.SMTP 3.MTA 4.SMTP 5.MTA 6.MDA 7.POP 8.MUA
· 1.MUA 2.POP 3.MDA 4.SMTP 5.MTA 6.MDA 7.SMTP 8.MUA
· None of the above
15. Which OSI layer addressing is required to route packets between two networks?
· Layer 4
· Layer 7
· Layer 1
· Layer 2
· Layer 3
16. A routing issue has occurred in your internetwork. Which of the following type of devices should be examined to isolate this error?
· Router
· Switch
· Access point
· Host
· Hub
17. Refer to the exhibit. The nslookup command that is shown was issued on a Windows PC host. What does the 10.32.5.74 address represent?

· the IP address of the host
· the IP address of host D
· the default gateway for the host
· the primary DNS server for the host
· the home page address for the host
18. What command can be used to troubleshoot domain name resolution issues?
· Tracert
· Nslookup
· Get
· Arp –a
· Arp -c
19. Which answer lists the CLI mode hierarchy from least level of privilege to greatest?
· global, privileged, user, specific
· user, privileged, global, specific
· global, user, privileged, specific
· user, global, privileged, specific
· specific, privileged, global, user
20. Refer to the exhibit. The ping 127.0.0.1 command is issued on the local host. What do the ping results indicate?
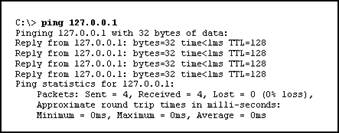
· The local host has full connectivity to the default gateway.
· The local host has full connectivity to the remote network.
· The local host can send packets on the local network.
· The TCP/IP stack on the local host operates properly.
· The TCP/IP stack has problems in network connectivity.
21. A user sees the command prompt: router(config-if)# . What task can be performed at this mode?
· Reload the device.
· Perform basic tests.
· Configure individual interfaces.
· Configure individual terminal lines.
· Examine running-configuration file.
22. What is the first thing that happens when a collision occurs in an Ethernet network?
· The transmitting devices immediately back off transmitting for a preset period of time??
· The transmitting devices continue to transmit to ensure that all devices on the network detect the collision.
· The transmitting devices invoke the backoff algorithm.
· The transmitting devices stop transmitting immediately.
· None of the above
23. A network technician is tasked with setting up a network for six users, but the users should be able to use their accounts to log on from any of the six computers. What type of network should be used?
· client-server network
· client-client network
· Workgroup
· P2P applications
· peer-to-peer network
24. Which option represents a point-to-point logical topology diagram?
· 
· 
· 
· 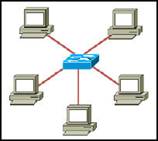
· None of the above
25. Refer to the exhibit. Which layered network model is shown in the diagram? 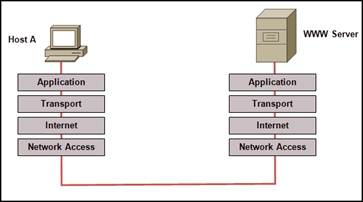
· SDIP
· OSI
· Cisco
· IETF
· TCP/IP
26. Refer to the exhibit. What function does router RT_A need to provide to allow Internet access for hosts in this network?

· Resolution of ISP’s ADs
· Address translation
· FTP
· Web server
· DHCP services
27. Which configuration mode is used to set a password to authenticate users that are accessing and configuring the network device using a Telnet connection?
· AUX
· VTY line mode
· console line mode
· global configuration mode
· interface mode
28. How many host addresses may be assigned when using the 128.107.0.0 network address with a subnet mask of 255.255.248.0?
· 30
· 4094
· 2048
· 4096
· 256
· 2046
29. In a network design project, a network designer needs to select a device to provide collision free connections to 40 hosts on the LAN. Which device should be selected?
· Hub
· Modem
· Router
· Switch
· Firewall
30. Which router configuration mode will require user authentication if an administrator issues the enable secret command?
· service specific configuration mode
· user executive mode
· privileged executive mode
· global configuration mode
· None of the above
31. Which application layer protocol allows administrators to log into a server from remote locations and control a server as though logged in locally?
· Telnet
· FTP
· DHCP
· DNS
· SMTP
32. What is the broadcast address for the network 172.16.70.32/28?
· 172.15.70.255
· 172.16.70.48
· 172.16.70.128
· 172.16.70.47
· 172.16.70.255
33. What type of IP address should be assigned to a web server?
· Nanocast
· Static
· Multicast
· Dynamic
· Broadcast
34. Refer to the exhibit. The network administrator remotely accesses the CLI of RouterB from PC1 using a secure connection. Which statement is true about this connection?
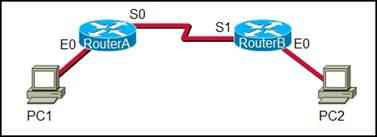
· The SSH service is used to connect PC1 to RouterB.
· The Telnet server process is running on PC1.
· The GET request is sent to RouterA to retrieve data.
· Only the exchange of the Telnet username and password is encrypted.
· None of the above.
35. Refer to the exhibit. Host A and B are unable to communicate with each other. What is the reason for this? 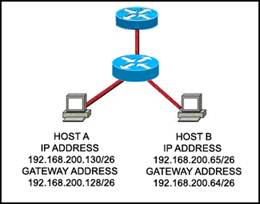
· The gateway addresses are network addresses.
· Host B is assigned a multicast address.
· Host A and host B belong to different networks.
· Host A is assigned a network address.
· None of the above
36. Refer to the exhibit. Which option shows the correct topology given the configuration of Router1? 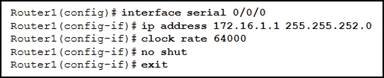
· 
· 
· 
· 
· None of the above
37. Which exhibit shows the interface that is configured by the command, router(config)# interface serial 0/0/1?
· 
· 
· 
· 
· 
38. Refer to the exhibit. When computer A sends a frame to computer D, what computers receive the frame? 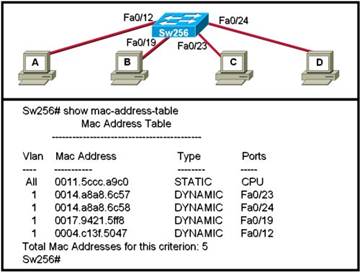
· Only computer A
· Only computer D
· Only computer A and computer D
· Only computer B, computer C, and computer D
· All computers
39. Refer to the exhibit. Host A is configured with the correct IP address for the default gateway of the router R1 FastEthernet0/1 interface. How will a packet that is sent from host A to host B be handled by the devices on the network?
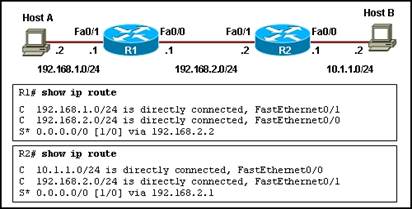
· R1 will drop the packet because R1 does not have a specific route in its routing table to the 10.1.1.0/24 network.
· R1 will forward the packet to its default gateway, the next hop router R2. R2 will drop the packet because it does not have a route that is learned by a routing protocol to network 10.1.1.0/24.
· R1 will forward the packet to its default gateway, the next hop router R2. R2 will forward the packet to the directly connected network 10.1.1.0/24.
· R1 will forward the packet to its default gateway, the next hop router R2. R2 will drop the packet because it does not have a default route to network 10.1.1.0/24.
· None of the above.
40. Which basic process is used to select the best path for forwarding data?
· Addressing
· Encapsulation
· Routing
· Switching
· Backoffing
41. Refer to the exhibit. Which Layer 2 protocol could be used inside network A and network C?
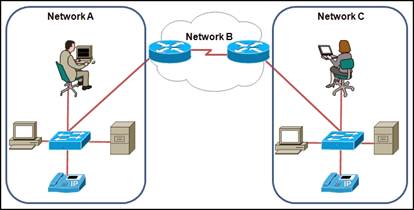
· IP
· Ethernet
· TCP
· UDP
· None of the above
42. Refer to the exhibit. Host C is able to ping 127.0.0.1 successfully, but is unable to communicate with hosts A and B in the organization. What is the likely cause of the problem?
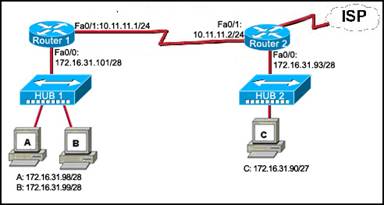
· The IP addresses on the router serial interfaces are wrong.
· The subnet mask on host C is improperly configured.
· Hosts A and B are not on the same subnet as host C.
· The FastEthernet interface fa0/0 of router 1 is wrongly configured.
· Host C and B are in one subnet
43. Which subnet mask should be used for a Class B network that is divided into subnets and will accommodate between 800 hosts and 1000 hosts?
· 255.255.255.0
· 255.255.248.0
· 255.255.240.0
· 255.255.254.0
· 255.255.252.0
44. How many bits belong to OUI in MAC address
· 48
· 24
· 1
· 2
· 96
45. Which command change mode to Console line configuration?
· Line vty 0 4
· Mode line console
· Line console configuration
· Console line 0
· Line console 0
46. Which Layer 4 protocol is used to transport voice packets in a VoIP deployment?
· UDP
· IP
· ARP
· TCP
· HTTP
47. How can ARP be used to help document the network?
· It can list each hop on the way to a destination host.
· It can provide a list of physical addresses on the network.
· It can indicate which hosts are not responding to network traffic.
· It can show the average latency of hosts on the network.
· None of the above.
48. The tracert 10.1.3.2 command was issued on computer A. Computer A can ping other addresses on the local subnet. Computer A sent the first ICMP packet toward computer B with a TTL value of 1. A protocol analyzer that was running on computer B showed that the packet never reached its destination. Why did the packet not reach the destination?
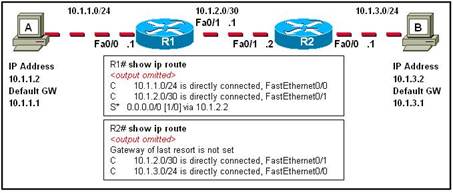
· R1 does not have a route for the destination network.
· The TTL for the packet was decreased to zero by R1.
· There is a TCP/IP problem on computer A.
· There is a routing loop between R1 and R2.
· None of the above
49. Refer to the exhibit. Host A is able to access resources on the local LAN but is unable to access any resources on the Internet. What is the likely cause of this problem? 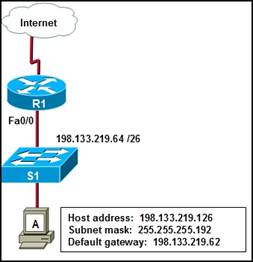
· The network uses private addresses.
· The host address is a network address.
· The default gateway is on a different subnet from the host.
· The host subnet mask in incorrect.
· None of the above.
50. When must a router serial interface be configured with the clock rate command?
· when the interface timers have been cleared
· when the connected DTE device is shut down
· when the interface is functioning as a DTE device
· when the interface is functioning as a DCE device
· None of the above
51. Which OSI layer does IP rely on to determine whether packets have been lost and to request retransmission?
· Session
· Transport
· Application
· Presentation
· Network
52. Refer to the exhibit. What is required on host A for a network technician to create the initial configuration on Router1?
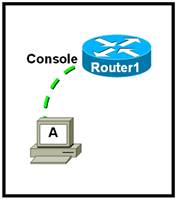
· Packet Tracer simulator
· An ftp client
· A web browser
· A telnet client
· A terminal emulation program
53. A technician wishes to connect two computers to move data from one to the other before reloading the operating system. The NICs on both PCs do not support autosensing feature. Which procedure will satisfy the requirement?
· Interconnect the two PCs with a crossover cable.
· Interconnect the two PCs with two crossover cables and a hub.
· Interconnect the two PCs with a rollover cable.
· Interconnect the two PCs with two rollover cables and a hub.
· None of the above
54. Which router component will have contents erased when the command erase startup-config is issued?
· Flash
· NVRAM
· RAM
· ROM
· DDRAM
55. Which service is used when the nslookup command is issued on a computer?
· FTP
· Telnet
· DNS
· DHCP
· HHTP
56. Which device should be used for enabling a host to communicate with another host on a different network?
· Router
· PC
· Switch
· Hub
· Host
57. Refer to the exhibit. The serial interface of the router was configured with the use of the commands that are shown. The router cannot ping the router that is directly connected to interface serial 0/0/0. What should the network technician do to solve this problem? 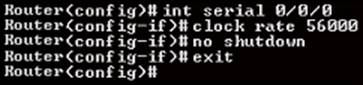
· Reboot PC.
· Configure the description at interface serial 0/0/0.
· Reboot the router.
· Configure an IP address on interface serial 0/0/0.
· Remove the no shutdown command at interface serial 0/0/0
58. Which router configuration mode would an administrator use to configure the router for SSH or Telnet login access?
· Privileged EXEC
· Router
· Global
· Line
· Interface
59. A network administrator is asked to design a new addressing scheme for a corporate network. There are 60 users in the main office, 40 users in the branch office, 28 users in manufacturing, 12 in the sales office, and 4 users in the research office. Which VLSM addressing scheme that uses the 192.168.88.0/24 network will fulfill the requirements while wasting the fewest addresses?
· 192.168.88.0/27 main
192.168.88.32/27 branch
192.168.88.64/28 manufacturing
192.168.88.80/29 sales
192.168.88.88/30 research
· 192.168.88.0/27 main
192.168.88.64/28 branch
192.168.88.80/28 manufacturing
192.168.88.96/29 sales
192.168.88.104/30 research
· 192.168.88.0/26 main
192.168.88.32/26 branch
192.168.88.64/26 manufacturing
192.168.88.96/27 sales
192.168.88.128/28 research
· 192.168.88.0/26 main
192.168.88.64/26 branch
192.168.88.128/27 manufacturing
192.168.88.160/28 sales
192.168.88.176/29 research
· None of the above
60. What type of network is maintained if a server takes no dedicated role in the network?
· Peer-to-peer
· Centralized
· Main frame
· Client/server
· None of the above
61. Refer to the exhibit. Which list refers only to end devices?
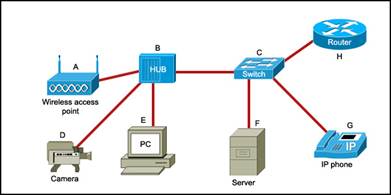
· G,D,D,T
· D,E,F,G
· A,D,E,G
· A,H,B,C
· A,D,E,F
62. Which topology represents a collision-free environment?
· 
· 
· 
· 
· None of the above
63. Refer to the exhibit. Host A attempts to establish a TCP/IP session with host C. During this attempt, a frame was captured with the source MAC address 0050.7320.D632 and the destination MAC address 0030.8517.44C4. The packet inside the captured frame has an IP source address 192.168.7.5, and the destination IP address is 192.168.219.24. At which point in the network was this packet captured? 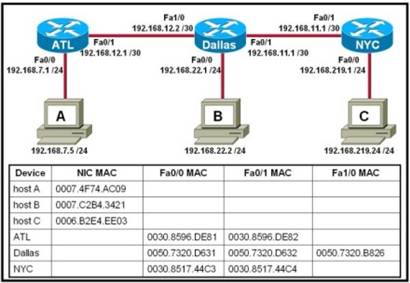
· Leaving NYC
· Leaving host A
· Leaving ATL
· Leaving Almaty
· Leaving Dallas
64. During the encapsulation process, which identifiers are added at the transport layer?
· two networks routing the packets
· two nodes on the local network exchanging the frame
· two applications communicating the data
· two hosts at either end of the communication
· None of the above
65. Which statement is true about router hostnames?
· A router hostname must be created before any other configurations can be added to the device.
· A hostname should be unique on each router.
· A router hostname cannot contain capital letters.
· A router hostname is configured in privileged executive mode.
· None of the above
66. Refer to the exhibit. When host A sends a frame addressed for host D, which hosts will receive the frame? 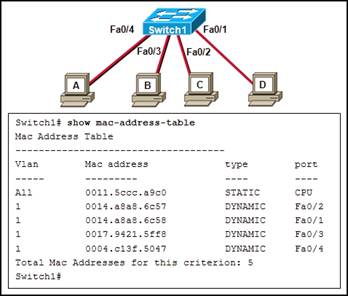
· Only hosts A and D
· Only hosts B, C, and D
· Only host D
· Only Host A
· All hosts
67. A technician is asked to secure the privileged EXEC mode of a switch by requiring a password. Which type of password would require this login and be considered the most secure?
· Disable
· Console
· Enable
· Enable secret
· VTY
68. Refer to the exhibit. A PC is connected to a network. Which action will verify that the PC can communicate with its default gateway?
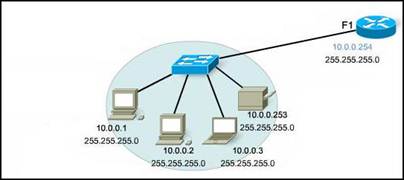
· Use the ping 10.0.0.254 command.
· Use the ping 127.0.0.1 command.
· Use the ipconfig command.
· Use the ipconfig/all command.
· None of the above.
69. Refer to the exhibit. Host A and B are unable to communicate with each other. What is the reason for this? 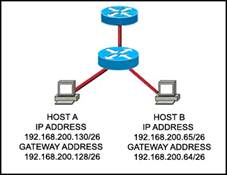
· The gateway addresses are network addresses.
· Host A is assigned a network address.
· Host B is assigned a multicast address.
· Host A and host B belong to different networks.
· None of the above
70. Which OSI layer manages data segments?
· Data-link layer
· Application layer
· Session layer
· Presentation layer
· Transport layer
71. By using the ipconfig command, a network administrator determines that a workstation has the address 192.168.3.38 with 29 bits set in the subnet mask. To what network does the workstation belong?
· 192.168.3.8
· 192.168.3.34
· 192.168.3.16
· 192.168.3.32
· 192.168.3.24
72. In which scenario would a crossover cable be required between Ethernet ports on the devices?
· Computer to switch
· Switch to router
· Computer to hub
· Computer to router
· None of the above
73. Which additional piece of information is included in the updates of classless routing protocols to support the use of VLSM and discontiguous networks?
· Neighbor router ID
· Metric
· Network mask
· Administrative distance
· None of the above
74. Refer to the exhibit. Hosts on the 192.168.1.0 network cannot communicate with hosts on the 172.16.1.1 network. The network administrator has run the show ip route command on R1. What could be the cause of this problem?

· The serial interface S0/0/0 of R1 is administratively down.
· The FastEthernet interface on R1 is disabled.
· Autosummarization is enabled on R1.
· No static route or routing protocol is configured.
· None of the above.
75. Refer to the exhibit. A network administrator is trying to determine why router JAX has no OSPF routes in its routing table. All routers are configured for OSPF area 0. From the JAX router, the administrator is able to ping its connected interfaces and the Fa0/1 interface of the ORL router but no other router interfaces. What is a logical step that the network administrator should take to troubleshoot the problem? 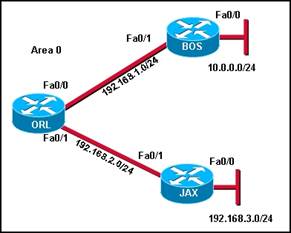
· Check to see if the cable is loose between ORL and JAX.
· Check to see if CDP packets are passing between the routers.
· Reboot the routers.
· Change the OSPF process ID on all of the routers to 0.
· Use show and debug commands to determine if hellos are propagating.
76. In a lab test environment, a router has learned about network 172.16.1.0 through four different dynamic routing processes. Which route will be used to reach this network?
· D 172.16.1.0/24 [90/2195456] via 192.168.200.1, 00:00:09, Serial0/0/0
· O 172.16.1.0/24 [110/1012] via 192.168.200.1, 00:00:22, Serial0/0/0
· R 172.16.1.0/24 [120/1] via 192.168.200.1, 00:00:17, Serial0/0/0
· I 172.16.1.0/24 [100/1192] via 192.168.200.1, 00:00:09, Serial0/0/0
· None of the above
77. Because of a topology change, the next hop IP address in the current static route must be reconfigured. How can a static route entry be altered to accommodate a topology change?
· Keep the existing static route and configure a new static route with the correct next hop IP address.
· Do nothing. The existing static route will automatically update the next hop entry with the new IP address.
· Keep the existing static route, reload the router, and configure a new static route with the correct next hop IP address.
· Negate the existing static route and configure a new static route with the correct next hop IP address.
· None of the above.
78. Which protocol is used by EIGRP to deliver and receive update packets?
· UDP
· FTP
· TFTP
· RTP
· TCP
79. What is a function of the console port on a router?
· It is used to manage the router.
· It is used for packet receiving and forwarding.
· It is used to interconnect various types of LANs.
· It is used to interconnect a variety of serial links including T1, DSL, and ISDN.
· None of the above.
80. Refer to the exhibit. Which summarization should R1 use to advertise its networks to R2?
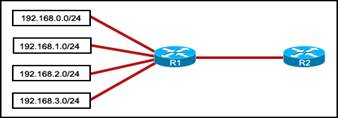
· 192.168.1.0/22
· 192.168.1.0/24
· 192.0.0.0/26
· 192.168.0.0/24
· 192.168.0.0/22
81. A network administrator is analyzing routing update behavior on a network that has both EIGRP and OSPF configured on all routers. Both protocols appear in the output of show ip protocols. However, only EIGRP internal routes appear in the routing tables. Which statement correctly explains the scenario?
· The EIGRP protocol has a lower administrative distance than OSPF.
· The OSPF protocol has a higher cost than EIGRP.
· The EIGRP protocol has a lower metric than OSPF.
· The EIGRP protocol was configured first on the router.
· None of the above.
82. Refer to the exhibit. Which path will traffic from the 172.16.1.0/24 network take to get to the 10.0.0.0/24 network?
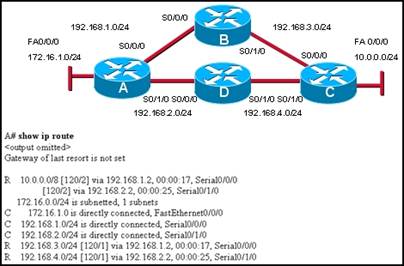
· It will load balance the traffic between ADC and ABC
· ADC
· ABC
· It will send the traffic via ABC, and will use ADC as a backup path only when ABC fails.
· None of the above.
83. Refer to the exhibit. After the commands are entered, which password will be required to establish a Telnet session with the router? 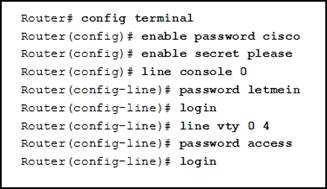
· Access
· Cisco
· Letmein
· VTY
· Please
84. Refer to the exhibit. Routers R1 and R2 are directly connected via their serial interfaces and are both running the EIGRP routing protocol. R1 and R2 can ping the directly connected serial interface of their neighbor, but they cannot form an EIGRP neighbor adjacency. 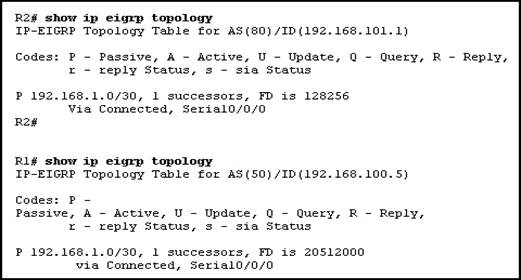
What action should be taken to solve this problem?
· Configure both routers with the same EIGRP process ID.
· Enable the serial interfaces of both routers.
· Configure EIGRP to send periodic updates.
· Configure the same hello interval between the routers.
· None of the above.
85. Refer to the exhibit. What is the purpose of the ip bandwidth-percent eigrp 50 10 command? 
· to limit the bandwidth EIGRP packets can use to 6.4 kb/s
· to limit the bandwidth EIGRP packets can use to 50 kb/s
· to limit the bandwidth EIGRP packets can use to 10 kb/s
· to limit the bandwidth EIGRP packets can use to 32 kb/s
· None of the above
86. Refer to the exhibit. Cost for each path are shown. If all routers are configured to use OSPF, what would be the path of a packet sent from Router C to Router D if Router A was down? 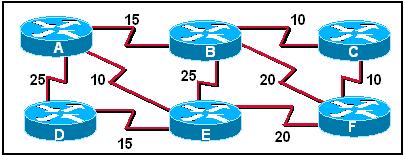
· C-F-B-A-D
· C-B-E-D
· C-F-E-A-D
· C-B-A-D
· C-F-E-D
87. Which router mode is accessed by entering the enable command?
· Interface configuration
· Privileged EXEC
· User EXEC
· Global configuration
· None of the above
88. Which statement is true about the metrics used by routing protocols?
· The router may use only one parameter at a time to calculate the metric.
· A metric is a value used by a particular routing protocol to compare paths to remote networks.
· The metric with the highest value is installed in the routing table.
· A common metric is used by all routing protocols.
· None of the above
89. A network administrator adds the default-information originate command to the configuration of a router that uses RIP as the routing protocol. What will result from adding this command?
· The router will only forward packets that originate on directly connected networks.
· The router will not forward routing information that is learned from other routers.
· The router will be reset to the default factory information.
· The router will propagate a static default route in its RIP updates, if one is present.
· None of the above.
90. Refer to the exhibit. R1 is configured properly for a single area OSPF, and R2 has been recently installed in the network. Which set of commands is required to configure a single area OSPF for the networks that are connected to R2? 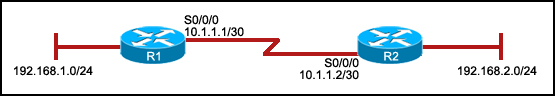
· R2(config)# router ospf 1
R2(config-router)# network 192.168.2.0 0.0.0.255 area 0
R2(config-router)# network 10.1.1.0 0.0.0.3 area 0
· R2(config)# router ospf 1
R2(config-router)# network 192.168.2.0 0.0.0.255 area 0
R2(config-router)# network 10.0.0.0 0.0.0.3 area 1
· R2(config)# router ospf 1
R2(config-router)# network 192.168.2.0 0.0.0.255 area 0
R2(config)# router ospf 2
R2(config-router)# network 10.1.1.0 0.0.0.3 area 0
· R2(config)# router ospf 1
R2(config-router)# network 192.168.2.0 0.0.0.255 area 0
R2(config-router)# network 10.1.1.0 0.0.0.3 area 1
· None of the above
91. Which command erase configurations which are stored in NVRAM memory?
· Delete NVRAM
· Delete running-config
· Erase NVRAM
· Erase startup-config
· Delete startup-config
92. Refer to the exhibit. If the EIGRP routing protocol is used throughout the network, which IP address and mask prefix should be sent by router R1 to the Edge router as a result of manual summarization of LANs A, B, C, and D?
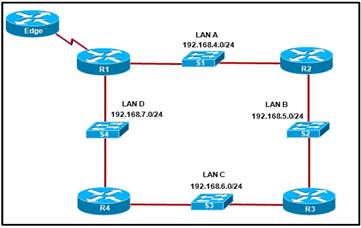
· 192.168.4.0/24
· 192.168.4.0/26
· 192.168.4.0/20
· 192.168.4.0/22
· 192.168.4.0/23
93. Which prompt is used to allow a user to change the IP address of an interface on a router?
· Router(config)#
· Router(config-if)#
· Router>
· Router#
· None of the above
94. Refer to the exhibit. Which route will be installed in the routing table on R1 to forward traffic from PC1 to the web server?

· the route learned via OSPF
· the route learned via EIGRP
· the static route
· both routes learned via OSPF and EIGRP
· None of the above
95. Because of a topology change, the next hop IP address in the current static route must be reconfigured. How can a static route entry be altered to accommodate a topology change?
· Keep the existing static route, reload the router, and configure a new static route with the correct next hop IP address.
· Do nothing. The existing static route will automatically update the next hop entry with the new IP address.
· Keep the existing static route and configure a new static route with the correct next hop IP address.
· Negate the existing static route and configure a new static route with the correct next hop IP address.
· None of the above.
96. Refer to the exhibit. The hosts that are connected to R2 are unable to ping the hosts that are connected to R1. How can this problem be resolved? 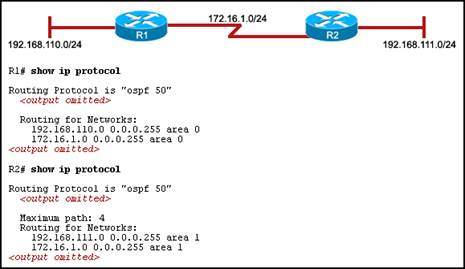
· Configure a loopback interface on both routers.
· Configure the router ID on both routers.
· Configure the R2 router interfaces for area 0.
· Configure the proper subnet masks on the router interfaces.
· None of the above
97. Refer to the exhibit. Which solution provides the most efficient use of router resources for forwarding traffic between BR and HQ? 
· RIP
· EIGRP
· Static routes
· RIPv2
· None of the above
98. Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols.
Which path will be used to transmit the data packets from PC1 to PC2? 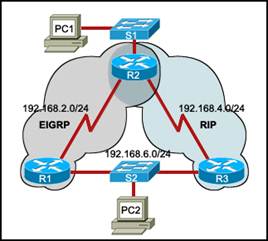
· The traffic will be load-balanced between two paths — via R2-R1 and via R2-R3.
· The packets will travel via R2-R3, and the other path via R2-R1 will be retained as the backup path.
· The packets will travel via R2-R1.
· The packets will travel via R2-R3.
· None of the above.
99. Refer to the exhibit. The network is configured with RIPv2. However, network administrators notice that communication cannot be successfully completed from one LAN to another. A network administrator issues the show ip route command on the HQ router. Based on the output, what should be done to correct the problem?
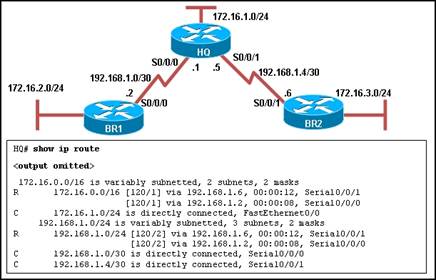
· Disable the load balancing feature of RIPv2.
· Replace RIPv2 with EIGRP which supports VLSM.
· Make sure that the network statements include the correct subnet mask.
· Issue the no auto-summary command for RIPv2.
· None of the above.
100. Which combination describes T568A UTP cable connection?
· Orange, white orange, green, white green, black, white black, blue,white blue
· White green, green, white orange, blue, white blue, orange, brown, white brown
· White green, green, white orange, blue, white blue, orange, white brown, brown
· White orange, orange, green, white green, blue, white blue, black, white black
· Orange, white orange, green, white green, black, white black, white blue, blue
Date: 2015-01-12; view: 2128
| <== previous page | | | next page ==> |
| Computer Engineering | | | COMPUTING AND SCHEMATIC PAPER |