
CATEGORIES:
BiologyChemistryConstructionCultureEcologyEconomyElectronicsFinanceGeographyHistoryInformaticsLawMathematicsMechanicsMedicineOtherPedagogyPhilosophyPhysicsPolicyPsychologySociologySportTourism
Talk about how some students may think they understand online safety, but unwittingly put themselves at risk.
Developing critical awareness of the internet. Readings, padletts
Lesson 2.
(Nozliya UzSWLU)
This lesson is devoted to matters of developing critical awareness of the internet materials. At the end of this lesson
-learners will be able to demonstrate an awareness of choosing relevant sources, and an appreciation of the need to make it meaningful and suitable to needs and interests;
- distinguish the main types of critical-thinking and decision-making skills relating to computer usage;
- demonstrate the safe and cooperative use of technology which helpes learners protect themselves from inappropriate behavior online.
- enhance outlook of learners about the potential risks for Internet users. and where they can obtain additional information and assistance regarding Internet safety.
Ñontent of the lesson
I. Spark
Challenge Problem
The rise of new information and communication technologies – social networking sites, Internet encyclopedias, multimedia-sharing facilities and databases – is said to be ‘ushering in a new era’. While new technology is meant to unlock our creative potential, bring us together and enlighten us, we also fear it is transforming our lives for the worse – dumbing down culture, destroying relationships and eroding privacy. Will new technology live up to our greatest expectations or fulfill our worst fears by transforming how we relate to one another? Do we risk confusing technological advances with sociological trends? Are we giving technology too much credit?
After explanation, teacher shows the list of ICT means and gives the following task:
DISCUSSION
1. Which of the advanced technologies (information and communication technologies (ICT) and scientific technology innovations) do you consider to be the most important? Which has changed the world the most? Mark them 1 for the important down to 5 for the least important.
 The computer (Internet)
The computer (Internet)
 The mobile phone
The mobile phone
 The television
The television
 The robots
The robots
 The products of nanotechnology
The products of nanotechnology
Students work in groups of 4-5. They are asked to persuade the others that their order is the right one.
Talk together as a group. What other technologies would you add to the list? Explain your answer.
In a globalized world, teachers must adapt their professional curriculum towards developing critical awareness. Critical awareness comprises the following aspects:
Ñritical thinking as comprising three essential parts. The first part was a problem-solving process in a context of interacting with the world and others. The second part was a reasoning process, informed by background knowledge, and previously acceptable conclusions which resulted in drawing a number of inferences through induction, deduction, and value judgment. The last part was a decision about what to do or what to believe.
It is regarded as the six elements of critical thinking as follows:
(1) Dispositions: Good critical thinkers are disposed to skepticism, questioning the accuracy, authenticity, plausibility, or sufficiently of whatever is presented to them.
(2) Criteria: Criteria are conditions that must be met for something to be judged as faithful or authentic.
(3) Argument: In critical thinking, an argument is a proposition with its supporting evidence and reasoning. The major purpose of an argument in critical thinking is to convince or persuade.
(4) Reasoning: Reasoning is what holds an argument together. We attempt to ascertain the strength of a conclusion by examining reasoning and logical relationships.
(5) Point of view: Point of view relates literally to the position from which a person perceives and makes meaning of things. A person’s point of view develops from prior experiences, cultural background, values, expectations, interests, and existing knowledge.
(6) Procedures for applying criteria and judgment: Socratic questioning is possibly the most broadly used procedure in critical thinking. This type of questioning seeks to clarify information, to identify a point of view, to discover assumptions, to distinguish factual claims from value judgments, and to detect flaws in reasoning.
How can the curriculum be adapted by critical awareness?
Compare your results with the following information:
Input
Criteria for evaluating and selecting Internet resources
It’s very difficult to create the authoring Internet-resources for the teaching aims, because the teacher him/herself should evaluate and select the teaching Internet resources. So, the following criteria help teachers.
Study the contents of the table below.
Guidelines to evaluate web site content of internet
| Criteria | Commentary |
| 1. The source of information. | Who is the author of the site, private personal or organization? Do you trust to this source? What interests is the placed in the sight information pursued for? |
| 2. Reliability of information. | What are the main arguments of the author of the site? Are there references to the other sources? What are they? Are they reliable? |
| 3. Topicality of information. | When was the information placed in the site? Is this information modern or old? |
| 4.Culturally-appropriateness of information. Cultural-conformity of information. | Is this information necessary for a certain stage and a level of education? Does this information provide the learners’ development? |
| 5. Objectiveness of information/audience survey. | Is material of site objective? Does it reflect the one position or contribute forming the whole pluralistic view on the reality? |
Analyze the web sites using the following guidelines:
Write about their strengths and weaknesses?
Face-to-face
II. Watch the video presentation on the theme “Internet safety”https://jr.brainpop.com/artsandtechnology/technology/internetsafety/and answer the following questions:
Do you think the average student in your grade level understands how to stay safe online? Have volunteers share their opinions and experiences in pairs or in a whole-class discussion.
Talk about how some students may think they understand online safety, but unwittingly put themselves at risk.
Students answer various open-ended questions about the video in terms of their personal enjoyment and the relevance of the content.
At this stage they are required to reflect and write about the context of the video, which encourages them to think critically about the subject.
III. Work in groups. Learners should describe advantages and disadvantages of each layer on the theme of internet safety. After implementing first stage of task they should demonstrate it.
Image Description:
A web of words with the words “Web-Web” written in the centre. The first layer surrounding the centre lists the ways in which people can interact online. The second layer lists possible issues people may encounter online.
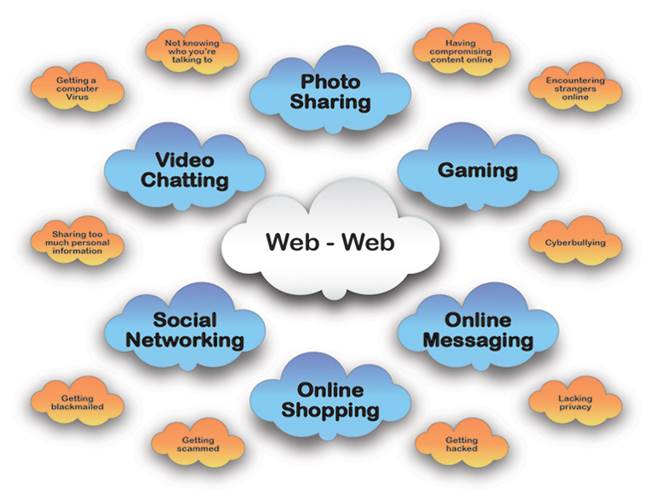
First layer:
· Social Networking
· Video Chatting
· Photo Sharing
· Gaming
· Online Messaging
· Online Shopping
Second layer:
· Phishing scams
· Having compromising content online
· Encountering strangers online
· Cyberbullying
· Lacking privacy
· Getting hacked
· Getting scammed
· Getting blackmailed
· Sharing too much personal information
· Getting a computer Virus
· Not knowing who you’re talking to
(full information about each item is available http://en.wikipedia.org/wiki/Internet_safety; https://sites.google.com/site/clasedespanolsenoracook/internet-safety)
Following questions will be given: What are your favorite things to do online? What is personal information? Why should you keep it private? What could you do to be safer online? What would you do if anyone online asked to meet you face-to-face? Besides me, who do you feel that you can talk to if you are in a scary or uncomfortable situation?
At the end ask learners to give examples of PRIVATE information that should never be shared online. The list should contain: phone number, address, full name, passwords, school name. Emphasize to students that nothing should be shared that could specifically identify them.
IV. Discussion. Study the following case studies which were recently published by WhoIsHostingThis.com that provides a number of statistics regarding internet privacy as well as tips on how to safely browse the web in 2014. And try to say which of these facing problems is the most dangerous.
Date: 2015-12-11; view: 1556
| <== previous page | | | next page ==> |
| Die Phoneme des Deutschen | | | Internet Safety Case Study 3 (safe and sane social networking) |