CATEGORIES:
BiologyChemistryConstructionCultureEcologyEconomyElectronicsFinanceGeographyHistoryInformaticsLawMathematicsMechanicsMedicineOtherPedagogyPhilosophyPhysicsPolicyPsychologySociologySportTourism
Protocols
To talk to each other, modems have to exchange a good bit of information, since there are so many different types and speeds of modems around. That's what the high pitched squeals and squawks are that you can hear when an analog modem is trying to connect. It's modem talk for "So, who are you? Do you speak my language? Well, maybe we can find a common language so these guys can get connected."
A digital modem does not make noises (an advantage!) but it must do the same kind of negotiation with the device at the other end to come up with a common language, called a protocol.
A protocol defines what information is exchanged and in what order. The names of the protocols are of the form v.##. So you'll see things like v.25bis, v.34, and v.120. Some protocols are more stable or faster than others at certain tasks.
Computer to Computer: Software
You can't just hook up your computer to a network or a modem and start sending and receiving data. The computer needs instructions on how to do this. You need some kind of communications software. Since there are a number of different communications tasks, there are different kinds of programs that manage those tasks.
Dialing
 Dialing software tells the computer how to place a call on the phone line connected to it. It also displays messages about the progress of the call or lack thereof. A list of phone numbers for frequently called, or frequently forgotten, numbers is an important feature.
Dialing software tells the computer how to place a call on the phone line connected to it. It also displays messages about the progress of the call or lack thereof. A list of phone numbers for frequently called, or frequently forgotten, numbers is an important feature.
These capabilities are often included in other software packages.
File Transfer
One of the most common uses of computer to computer communications is to transfer files from one to the other.
Downloading means to transfer a file to your computer from elsewhere.

| Uploading means to transfer a file from your computer to another.

|
Programs that manage this process include many file management features. You need to be able to see what files are available, their sizes, and the folders you can put the transferred file in. You may want to rename the file or create a new folder for your new file.
Such a program will also handle the process of connecting to the other computer. Many of the names of these programs include the letters FTP, which stands for File Transfer Protocol. (Yes, another kind of protocol. And there are more!!)
Terminal Emulation
Programs running on a network often make an assumption about what kind of keyboard is being used. Keyboards for terminals used on networks often have assigned special functions to certain keys. They may even have keys that don't exist on standard keyboards. In order to work with the network programs, you need a program that will disguise your keyboard and make the network think that you are one of them! You must emulate, that is mimic, the keyboard that is expected.
A terminal emulation program will make:

| look like | 
| to the network. |
Data Encryption

When sending data over a communications channel, there is always the possibility that someone will see your data that you didn't mean to. If your data is of a sensitive nature, like your credit card number, or if it is secret, like the formula for Coca-Cola, you'd probably like to keep strangers from reading it.
A data encryption program encodes your data, just like spies do. So to read it, a person would need the right decoding program and the right password or file to give that program so it would know what to do exactly.
Computer to Computer: Networks
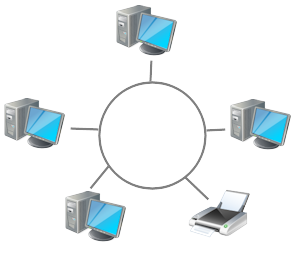
A network is a set of computers which are linked together on a permanent basis. This can mean two computers cabled together on the same desk, or thousands of computers across the world. The connections can be cables or wireless.

Network made up of a server, connected desktop computers,
a shared network printer, a laptop connected wirelessly
| Advantages: |
|
| Disadvantages: |
|
LAN
| A LAN is a Local Area Network. This would include networks where the computers are relatively close together. So LANs would be within the same office, a single building, or several buildings close together. The graphic at the right shows two buildings with 4 departments connected as a LAN that uses 3 servers. A small LAN is often set up just to provide Internet access to all the computers in a small office or a home. Sharing a printer or scanner is also a good reason for a small LAN. | 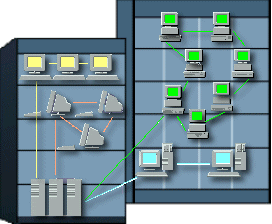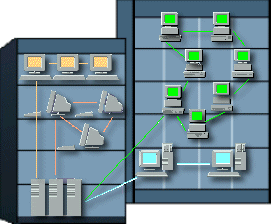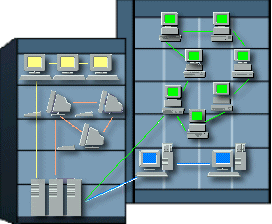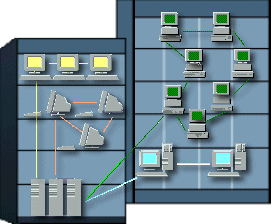
|
WAN
| A WAN is a Wide Area Network, which would be all networks too large to be LANs. There doesn't seem to be a clear line between the two designations. A WAN would be most useful for large companies with offices or factories in widely separated areas, like Microsoft, IBM, Ford, AT&T, etc. The same advantages apply as for a LAN except that a WAN would not share an Internet connection. Often a WAN uses the Internet to connect with instead of dedicated cables between far distant computers. But you can still set up remote access for computers and hardware over a WAN. | 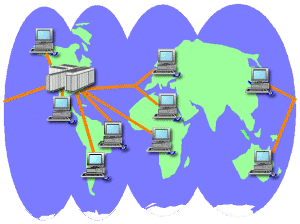
|
Computer to Computer: Network Configurations
There are a number of ways that computers can be connected together to form networks.
The pattern of connections depends in part on the distances involved since that determines what hardware must be used. It also depends on the degree of stability needed for the network. That is, how important is it that the whole system can't crash at the same time. These choices carry dollar costs, too. Better costs more, sometimes a LOT more.
Each device in the network, whether it's a computer, printer, scanner, or whatever, is called a node.
Star
 The star pattern connects everything to a host computer, a network switch, or a network hub, which handles the network tasks. All communications between computers go through the host/switch/hub. This configuration is good for home networks, often using a wireless hub instead of a host computer. Using a very large host computer, it is good for businesses that have large amounts of rapidly changing data, like banks and airline reservation offices.
The star pattern connects everything to a host computer, a network switch, or a network hub, which handles the network tasks. All communications between computers go through the host/switch/hub. This configuration is good for home networks, often using a wireless hub instead of a host computer. Using a very large host computer, it is good for businesses that have large amounts of rapidly changing data, like banks and airline reservation offices.
| |||||||||||||||||
| Advantages: |
| ||||||||||||||||
| Disadvantages: |
| ||||||||||||||||
Bus
Ring
Connecting Networks Networks can be connected to each other, too. There are difficulties in doing so, however. A combination of software and hardware must be used to do the job.
Suppose the accounting, advertising, and shipping departments of a company each have networks of PCs. These departments need to communicate with each other, but only sometimes. It would be easier and cheaper to connect them to each other than to put them all on the same larger network. The best arrangement would be for the departmental networks to be of the same kind so that a bridge could be used. |
Computer to Computer: Network Servers
Problem: You need a list of customers who have outstanding balances with your company of over $1000.
If you are on a network, what happens when you request data depends on the setup of the host computer, the server. A server is usually faster and more powerful than the computers connected to it on the network.
File Server
When you ask for customers with outstanding balances of over $1000, a computer set up as a file server will send out a copy of the whole Customers file to your computer. Your computer does the search through the file for the customers that meet the criteria of "Balance > $1000".
This is fine unless the Customers file is large. Then it would take a long time just to download the file to your computer. It would also take a long time to search through such a large file.
 Click each step below to see how a File Server works.
Click each step below to see how a File Server works.



Client Server
When you ask for the customers with balances of over $1000, a computer set up as a client server does the search itself and sends only the results to your computer.
This is best when the file is large or changes rapidly. It takes advantage of the extra power of the server and avoids the "dead time" of a long download.
 Click on each step below to see how a Client Server works
Click on each step below to see how a Client Server works



Date: 2015-01-11; view: 2161
| <== previous page | | | next page ==> |
| Types of Digital Modems | | | Computer to Computer: Summary |