
CATEGORIES:
BiologyChemistryConstructionCultureEcologyEconomyElectronicsFinanceGeographyHistoryInformaticsLawMathematicsMechanicsMedicineOtherPedagogyPhilosophyPhysicsPolicyPsychologySociologySportTourism
An Overview of the Microsoft's CryptoAPI
Microsoft's CryptoAPI allows independent software vendors (ISVs) to dynamically load Cryptographic Serivce Providers (CSPs) as in the following diagram:
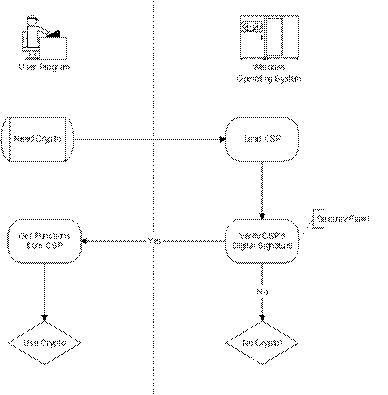
This arrangement of having Windows verify the CSP signature is what allows Microsoft to add cryptographic functionality to Windows. They will not digitally sign a CSP unless you first agree to abide by US export rules. Translation: Microsoft will not allow non-US companies to add strong crypto functions to Windows.
Fortunately, the verification of the CSP's digital signature opens up a security flaw in this picture.
Observations
Using NT4 Server, SP5 (domestic, 128-bit encryption version), and Visual C++ 6, SP3. These same results have been found in Win95osr2, Win98, Win98gold, WinNT4 (all versions), and Win2000 (up to and including build 2072, RC1).
Many people have emailed us to say that these debugging symbols are actually present in NT4-Workstation, and are in the original CD's debugging symbols! Thanks, people!
| Before CSP loading | in ADVAPI32.DLL | |
| Address 0x77DF5530 | -> | A9 F1 CB 3F DB 97 F5 ... ... ... |
| Address 0x77DF55D0 | -> | 90 C6 5F 68 6B 9B D4 ... ... ... |
| After RC4 encryption using | we see | |
| A2 17 9C 98 CA | => | R S A 1 ... 00 01 00 01 ... (looks like an RSA public key) |
| A0 15 9E 9A C8 | => | R S A 1 ... 00 01 00 01 ... (looks like an RSA public key) |
| Looking at SP5 debugging symbols | in "_CProvVerifyImage@8" | |
| Address 0x77DF5530 | <- | has data tag "_KEY" |
| Address 0x77DF55D0 | <- | has data tag "_NSAKEY" |
Screenshots One, Two, Three, Four, and Five showing the actual debugging information.
The Flaw
An attack:
Replace "_KEY" with your own key...
...but Windows will stop working since it cannot verify its own security subsystem!
An better attack:
Replace "_NSAKEY" with your own key...
... Windows keeps working, since Microsoft's key is still there
stops the NSA
works because Windows tries to verify the CSP first using "_KEY", and then silently fails over to "_NSAKEY"
The Result:
Windows CryptoAPI system still functional
the NSA is kicked out
the user can load an arbitrary CSP, not just one that Microsoft or the NSA signed!
Implications
What is the purpose of "_NSAKEY"? Espionage? Or do they simply not want to rely on Microsoft when installing their own CSPs?
Using RSA's Data Security's (now Security Dynamics) "BSafe" toolkit actually makes analysis of a program easier.
We do not need to modify the "advapi32.dll" file in order to remove the NSA key, nor do we need special privilleges on the machine.
use self-modifying code
needs undocumented vxd calls under Win95 and Win98
needs special memory features under WinNT and Win2k
It is easy for any process to bypass any CSP and substitute its own.
Export control is effectively dead for Windows.
Note for Win2k - there appear to be three keys in Win2k; Microsoft's, the NSA's, and an unknown third party's. Thanks to Nicko van Someren for bringing this to our attention.
Removing the NSA.
A sample program which temporarily replaces the NSA key with a test key, and leaves the rest of the CryptoAPI system intact, can be downloaded by clicking this link (currently only for WinNT and Win2k).
For legal reasons, source code will be provided for free, but only be available through a Nondisclosure Agreement with Cryptonym. You can download the NDA here in Word/Wordperfect RTF format, PostScript PS format, or Acrobat PDF format. Make sure you initial all pages, and fax it to the phone number indicated.
These files are provided for demonstration purposes only, and may not be redistributed or used for any purpose other than demonstration without the written authorization and license of Cryptonym Corporation.
Date: 2015-02-16; view: 1285
| <== previous page | | | next page ==> |
| Microsoft, the NSA, and You | | | What Public Speaking Has to Offer You |